DISCLAIMER : Please note that blog owner takes no responsibility of any kind for any type of data loss or damage by trying any of the command/method mentioned in this blog. You may use the commands/method/scripts on your own responsibility.If you find something useful, a comment would be appreciated to let other viewers also know that the solution/method work(ed) for you.
Running Commands as Another User via sudo
You want one user to run commands as another, without sharing passwords.
Suppose you want user smith to be able to run a given command as user jones.
The ALL keyword, which matches anything, in this case specifies that the line is valid on any host.
sudo exists for this very reason!
To authorize root privileges for smith, replace “jones” with “root” in the above example.
Suppose you want user smith to be able to run a given command as user jones.
/etc/sudoers:
smith ALL = (jones) /usr/local/bin/mycommandUser smith runs:smith$ sudo -u jones /usr/local/bin/mycommand
smith$ sudo -u jones mycommand If /usr/local/bin is in $PATHUser smith will be prompted for his own password, not jones’s. The ALL keyword, which matches anything, in this case specifies that the line is valid on any host.
sudo exists for this very reason!
To authorize root privileges for smith, replace “jones” with “root” in the above example.
Kubectl commands - Kubernetes
Kubectl is a command line interface for running commands against Kubernetes clusters. This overview covers
kubectl syntax, describes the command operations, and provides common examples. For details about each command, including all the supported flags and subcommands, see the kubectl reference documentation.List all services
kubectl get services
kubectl get svcList everything
kubectl get all --all-namespacesDescribe service <name>
kubectl describe svc <name>Get services sorted by name
kubectl get services –sort-by=.metadata.nameList all pods
kubectl get podsWatch nodes continuously
kubectl get pods -wGet version information
kubectl get versionGet cluster information
kubectl get cluster-infoGet the configuration
kubectl config viewOutput information about a node
kubectl describe node <node-name>List the replication controllers
kubectl get rcList the replication controllers in specific <namespace>
kubectl get rc -n <namespace-name>Describe replication controller <name>
kubectl describe rc <name>Delete pod <name>
kubectl delete pod <name>Delete replication controller <name>
kubectl delete rc <name>Delete service <name>
kubectl delete svc <name>Remove <node> from the cluster
kubectl delete node <name>Show metrics for nodes
kubectl top nodesShow metrics for pods
kubectl top podsWatch the Kublet logs
watch -n 2 cat /var/log/kublet.logGet logs from service <name>, optionally selecting container <$container>
kubectl logs -f <name> [-c <$container>] execute <command> on <service>, optionally selecting container <$container>
kubectl exec <service> <command> [-c <$container>]Initialize your master node
kubeadm initJoin a node to your Kubernetes cluster
kubeadm join --token <token> <master-ip>:<master-port>Create namespace <name>
kubectl create namespace <namespace>Allow Kubernetes master nodes to run pods
kubectl taint nodes --all node-role.kubernetes.io/masterReset current state
kubeadm resetList all secrets
kubectl get secretsLaunch a pod called <name> ,using image <image-name>
kubectl run <name> --image=<image-name>Create a service described in <manifest.yaml> file
kubectl create -f <manifest.yaml>Validate yaml file with dry run
kubectl create --dry-run --validate -f sysaix.yamlScale replication controller
kubectl scale rc <name> --replicas=<count>Stop all pods on specific pods
kubectl drain <n> --delete-local-data --force --ignore-deamonsetsExplain resource
kubectl explain pods
kubectl explain svcOpen a bash terminal in a pod
kubectl exec -it sysa'xpod shCheck pod environment variables
kubectl exec sysaixpod envFilter pods by label
kubectl get pods -l owner=emreList statefulset
kubectl get stsScale statefulset
kubectl scale sts <stateful_set_name> --replicas=5Delete statefulset only (not pods)
kubectl delete sts <stateful_set_name> --cascade=falseView all events
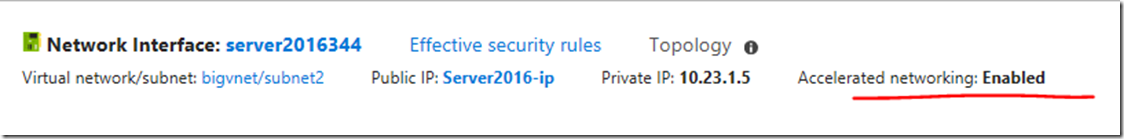
kubectl get events --all-namespacesHow to enable Accelerated Networking on an existing VM - AZURE
First, not all VM size support Accelerated Network, the supported OS and VM size can be found here:
https://docs.microsoft.com/en-us/azure/virtual-network/create-vm-accelerated-networking-cli
https://docs.microsoft.com/en-us/azure/virtual-network/create-vm-accelerated-networking-powershell
so I’ve deallocate the VM and change the size to DS3 v2, that’s a supported VM size.

Then run the following PowerShell Commands
https://docs.microsoft.com/en-us/azure/virtual-network/create-vm-accelerated-networking-cli
https://docs.microsoft.com/en-us/azure/virtual-network/create-vm-accelerated-networking-powershell
so I’ve deallocate the VM and change the size to DS3 v2, that’s a supported VM size.

Then run the following PowerShell Commands